
Compliance with Cybersecurity Standards: Protecting Organizations and Stakeholders
Introduction
Compliance with cybersecurity standards plays a critical role in safeguarding organizations and their stakeholders against the ever-growing threat landscape. In this comprehensive guide, we will explore the importance of complying with these standards, delve into the historical background that influenced their development, and discuss key concepts and definitions related to compliance.
Historical Background
The necessity for cybersecurity standards emerged in the early days of computing as the need to protect sensitive information became evident. Throughout history, significant milestones and events have shaped the current landscape of compliance. With the rise of cyberattacks and data breaches, frameworks and guidelines were established to mitigate risks and enhance cybersecurity measures.
Key Concepts and Definitions
To grasp the significance of compliance, it is crucial to understand the purpose of cybersecurity standards. These standards provide organizations with guidelines and best practices to ensure the confidentiality, integrity, and availability of their data and systems. Key terms such as risk assessment, vulnerability management, and incident response are essential in the compliance process.

Main Discussion Points
Point: Overview of Cybersecurity Standards and Frameworks
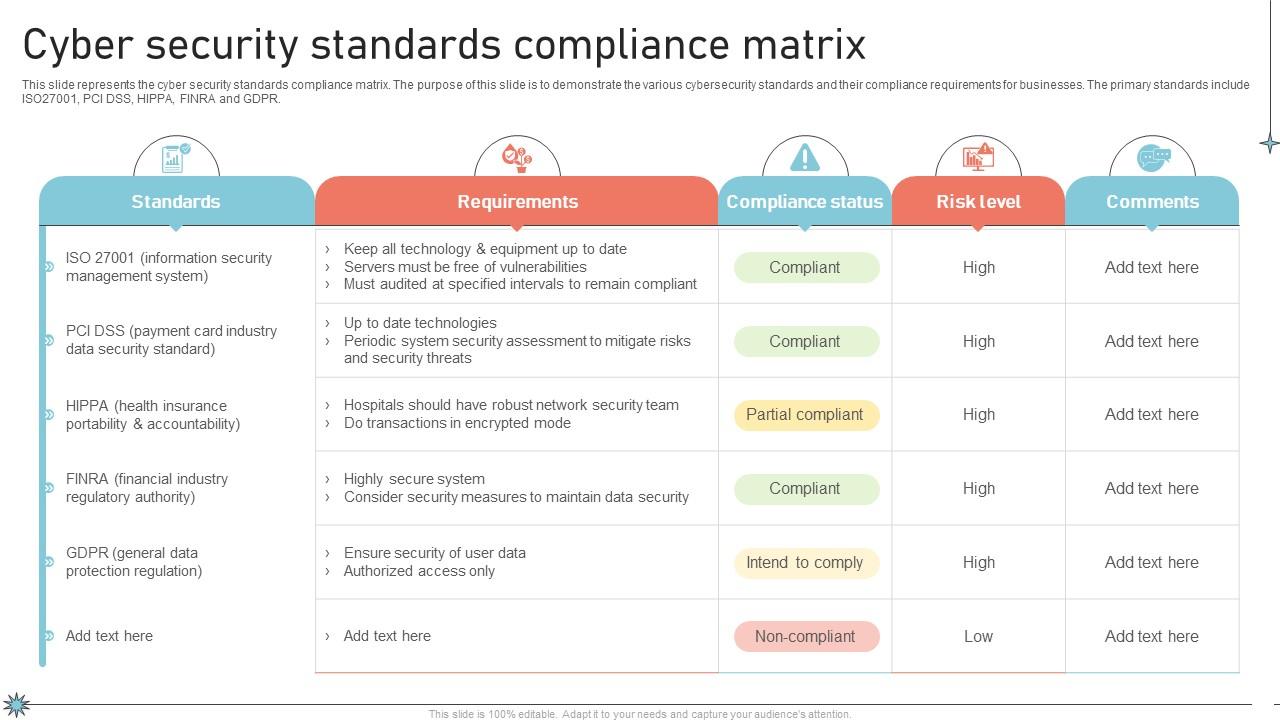
Numerous cybersecurity standards and frameworks have gained recognition in the industry. ISO 27001, NIST Cybersecurity Framework, and GDPR are among the most widely adopted standards. Each standard has its own objectives and requirements that organizations must adhere to in order to achieve compliance.
Point: Benefits of Compliance with Cybersecurity Standards
Compliance with cybersecurity standards brings numerous benefits to organizations. It significantly reduces the risk of cyberattacks and data breaches by implementing robust security measures. Moreover, compliance enhances the trust of stakeholders, including customers, partners, and investors, leading to potential cost savings and increased business opportunities.
Point: Challenges in Achieving Compliance
While compliance is crucial, organizations often face challenges while striving to meet the standards. Common obstacles include resource constraints and the complexity of the standards. Continuous monitoring and updating of compliance practices are essential to ensure ongoing adherence to the standards and mitigate emerging risks.
Case Studies or Examples
Real-world examples of organizations that have successfully implemented cybersecurity standards serve as inspirations for others. These organizations have experienced the positive impact of compliance on their cybersecurity posture and overall business operations. By learning from their success stories, organizations can gain insights into effective compliance strategies.
Current Trends or Developments
The field of cybersecurity is constantly evolving, and so are the standards and compliance requirements. It is essential for organizations to stay up-to-date with the latest trends and developments in the industry. Emerging technologies and practices, such as artificial intelligence and cloud security, play a pivotal role in shaping compliance efforts.
Challenges or Controversies
The effectiveness of cybersecurity standards has been a subject of debate in the industry. Some argue that compliance alone is not enough to protect against sophisticated cyber threats. Differing viewpoints on the value of compliance and potential alternatives, such as risk-based approaches, present challenges that organizations must navigate.
Future Outlook
Looking ahead, compliance with cybersecurity standards will continue to be of paramount importance. The rapidly evolving threat landscape and regulatory environment necessitate the development of new standards and frameworks. Organizations must anticipate potential developments and adapt their compliance practices to stay resilient in the face of emerging threats.
Conclusion
Compliance with cybersecurity standards is essential for organizations to protect themselves and their stakeholders from cyber threats. By understanding the historical background, key concepts, and current trends, organizations can navigate the challenges and controversies surrounding compliance. Ongoing commitment to maintaining robust security measures is crucial as the future implications of compliance shape the cybersecurity landscape.
References
ISO/IEC 27001:2013 – Information technology — Security techniques — Information security management systems — Requirements
NIST Cybersecurity Framework
General Data Protection Regulation (GDPR)
Ponemon Institute’s Cost of Data Breach Study
“The Role of Compliance in Cybersecurity” – Harvard Business Review




