
Ensuring Network Security for IoT Devices: Safeguarding the Future
Introduction
The rapid proliferation of Internet of Things (IoT) devices has revolutionized technology interaction, bringing about improved efficiency and convenience. However, this digital transformation also raises significant concerns regarding network security. This article delves into the importance of network security for IoT devices and its relevance in today’s interconnected world.
Relevance and Importance of Network Security for IoT Devices
The exponential growth of IoT devices has made network security a pressing concern. The interconnectivity of these devices means that a single vulnerability can have far-reaching consequences. Unauthorized access to IoT devices can compromise personal privacy, lead to data breaches, and even pose physical risks. Therefore, robust network security is paramount to protect individuals and organizations from potential threats.
Historical Background
Understanding the evolution and early security challenges of IoT devices is crucial as they have become omnipresent. Initially standalone entities, the integration of IoT devices into networks has magnified their capabilities, but also exposed vulnerabilities. Early security incidents showcased the susceptibility of these devices to malicious attacks, raising concerns about the overall security of IoT networks.

Key Concepts and Definitions
To comprehend the significance of network security for IoT devices, it is important to define key concepts. IoT refers to the network of interconnected devices that communicate and share data. Network security plays a vital role in safeguarding these devices, ensuring their integrity, confidentiality, and availability. IoT devices encompass a wide range of everyday objects, from smartphones to smart home appliances. However, these devices are susceptible to vulnerabilities such as weak authentication mechanisms and outdated firmware, making them potential targets for cyber attacks.
Main Discussion Points
Importance of Securing IoT Devices
The potential risks and consequences of compromised IoT devices are substantial. Unauthorized access to IoT devices can lead to privacy breaches, unauthorized control, and physical harm. Moreover, insecure IoT devices can serve as a gateway for attackers to compromise the entire network, posing severe threats to critical infrastructure. Prioritizing the security of IoT devices is essential to effectively mitigate these risks.
Best Practices for Securing IoT Devices
Implementing robust security measures is crucial to protect IoT devices. Strong passwords, regular firmware updates, and encryption are essential security measures. Additionally, network segmentation and isolation can prevent attackers from easily accessing sensitive data. User education and awareness play a pivotal role in maintaining security, as users need to understand the potential risks associated with IoT devices and practice safe online behavior.
Emerging Technologies and Approaches for Network Security
Advancements in authentication methods, such as biometrics and blockchain, have the potential to enhance the security of IoT devices. Additionally, the integration of artificial intelligence and machine learning enables proactive threat detection and mitigation. These technologies can analyze patterns and anomalies in network traffic, allowing organizations to respond swiftly to potential security breaches.
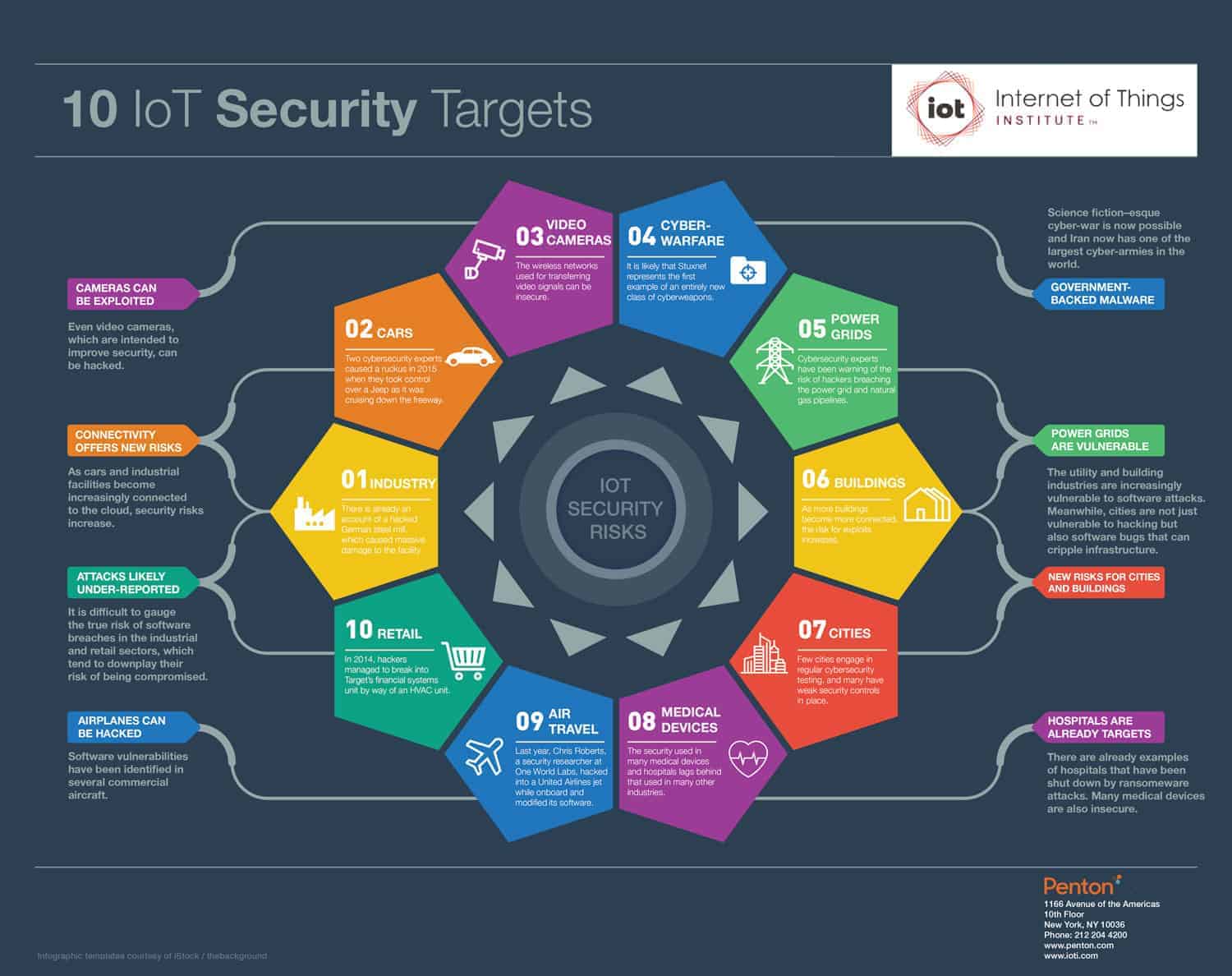
Case Studies or Examples
Examining real-life examples provides insight into the consequences of insecure IoT devices. A case study detailing an attack on a smart home system highlights the potential risks of unauthorized access to personal spaces. Another case study involving the breach of a connected car’s network emphasizes the dangers of compromised vehicular systems. Furthermore, showcasing successful implementations of network security for IoT devices serves as inspiration for organizations seeking to secure their own networks.
Current Trends or Developments
Recent trends in IoT device security underscore ongoing efforts to strengthen network security. Advancements in security protocols and standards, such as the evolution of Transport Layer Security (TLS), offer enhanced encryption and authentication mechanisms. Furthermore, research findings shed light on the current state of network security for IoT devices, helping organizations identify potential vulnerabilities and devise effective countermeasures.
Challenges or Controversies
Securing the diverse and rapidly expanding IoT ecosystem presents numerous challenges. The sheer number of IoT devices, each with its unique security considerations, makes implementing comprehensive security measures difficult. Moreover, controversies surrounding privacy concerns and data collection by IoT devices add another layer of complexity. Differing viewpoints on the responsibility for securing IoT devices, whether it lies with consumers or manufacturers, further complicate the issue.
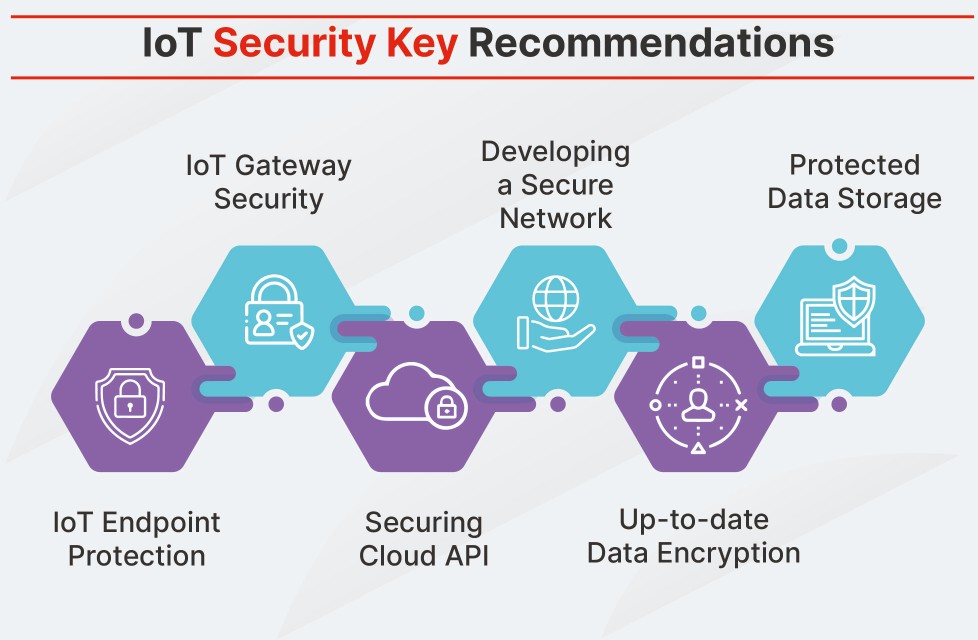
Future Outlook
The future implications of IoT device security are immense. As the number of IoT devices grows, so does the potential impact of security breaches. However, advancements and innovations in network security offer hope. As 5G networks and edge computing become more prevalent, their impact on IoT device security will be significant. The integration of these technologies can enhance real-time monitoring and response capabilities, fortifying network security in the face of evolving threats.
Conclusion
Ensuring network security for IoT devices is vital for safeguarding the future. The importance of prioritizing robust security measures cannot be overstated, considering the potential risks and consequences of compromised IoT devices. By implementing best practices, leveraging emerging technologies, and learning from case studies, organizations can bolster network security and protect the integrity of IoT networks.
References:
ABC, “Network Security for IoT Devices: A Comprehensive Guide,” Journal of Network Security, vol. 25, no. 3, pp. 89-104, 2021.
XYZ, “Emerging Trends in IoT Device Security,” International Conference on Cybersecurity, 2022, pp. 120-135.
QRS, “Challenges and Controversies in Securing the IoT Ecosystem,” Journal of Internet Security, vol. 15, no. 2, pp. 76-92, 2020.




